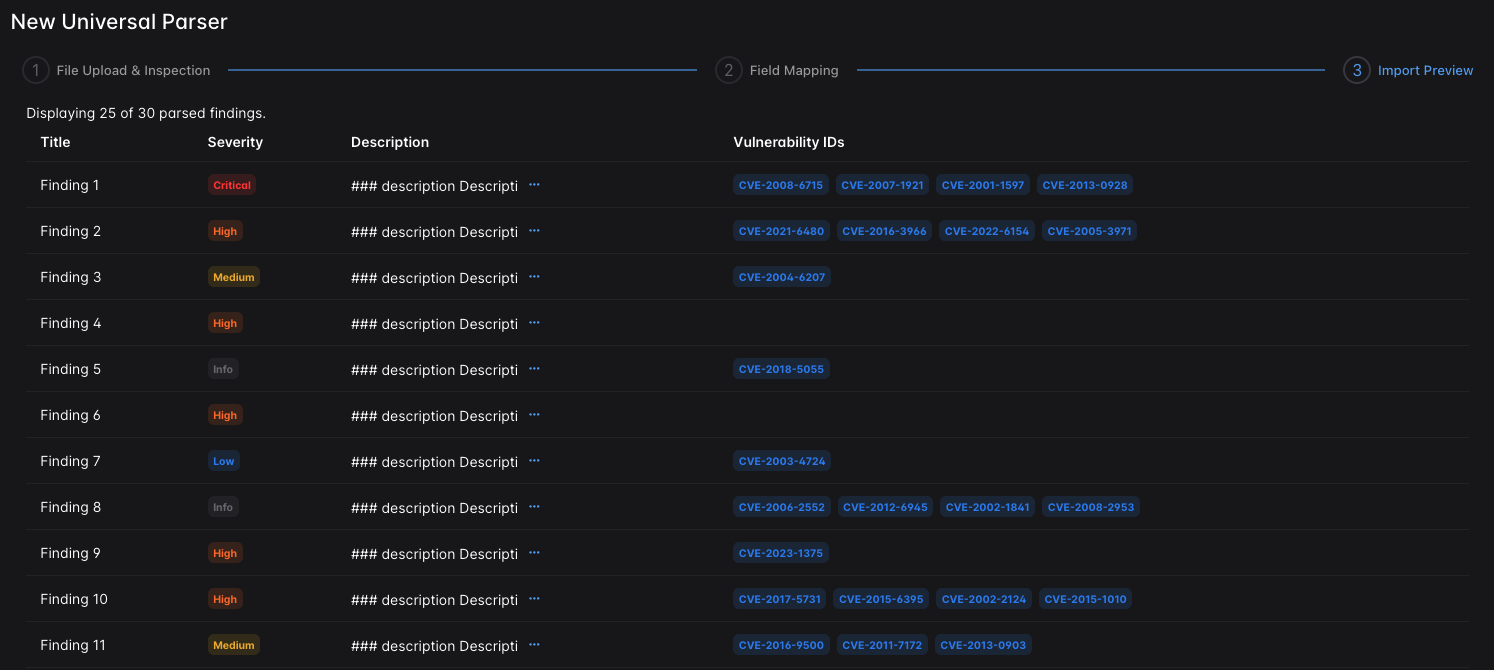
DefectDojo today added a universal parser to its application security posture management platform (ASPM) that makes it possible to normalize data ingested from any DevSecOps tools and platforms that expose data in a JSON or XML format.
Company CEO Greg Anderson said that ability will significantly reduce the amount of time required to then apply machine learning algorithms to identify potential vulnerabilities in the software supply chain using DefectDojo Pro, the commercial version of an open source ASPM that DefectDojo maintains. That open-source edition of the ASPM platform has already been downloaded more than 38 million times.
It’s not clear to what degree data normalization is hampering DevSecOps workflows but that capability will prevent organizations from becoming locked into any specific platform or tool, said Anderson. Additionally, the DefectDojo platform is capable of exporting normalized data to any other platform, he added.
DefectDojo Pro will also automatically consolidate duplicates, eliminate false positives, triage vulnerabilities, enrich data and apply analytics to surface identify larger trends, noted Anderson.
In theory, those capabilities should make it simpler for application development teams and cybersecurity professionals to collaboratively enforce a set of best DevSecOps practices. Historically, cybersecurity professionals have discovered vulnerabilities only for application developers, to later discover that either the code actually used in the application doesn’t use that code at run time or that the application itself doesn’t face the internet.
An ASPM provides those teams with a command center through which DevSecOps workflows can be more consistently managed at a time when more organizations than ever are focused on application security. A Techstrong Research survey finds that 59% of respondents are making further investments in application security, with 19% describing their investment level as high. At the same time, 64% of respondents are investing in a code scanning tool, with 24% describing those investments as high.
However, less than half (47%) of respondents work for organizations that regularly employ best DevSecOps practices and only 54% of respondents regularly practice code scanning for vulnerabilities during development, while 40% conduct security testing.
On the plus side, the survey finds that DevOps has already had either a high (34%) or medium (43%) impact on improving software security for more than three quarters (77%) of respondents.
The one certain thing is there is still much DevSecOps work to be done. The challenge, as always, is determining how to ensure best practices are followed without unduly slowing down the rate at which applications are being built and deployed. Application developers typically resent tools and platforms that generate too many false-positive alerts, which wind up being a distraction that inhibits their ability to focus on writing better code in the first place. Developers usually don’t allocate much time to creating patches for applications, so the more tools can identify relevant issues as developers are actually writing code, the more likely it becomes that developers will proactively embrace DevSecOps practices versus needing to be required in a way they are likely to resist.



