OpenText has partnered with Secure Code Warrior to make it simpler for application developers to learn best DevSecOps practices as needed.
Dylan Thomas, senior director of product and engineering at OpenText, said organizations that adopt Open Fortify code scanning tools and services can now seamlessly give developers access to the security training tools created and maintained by Secure Code Warrior.
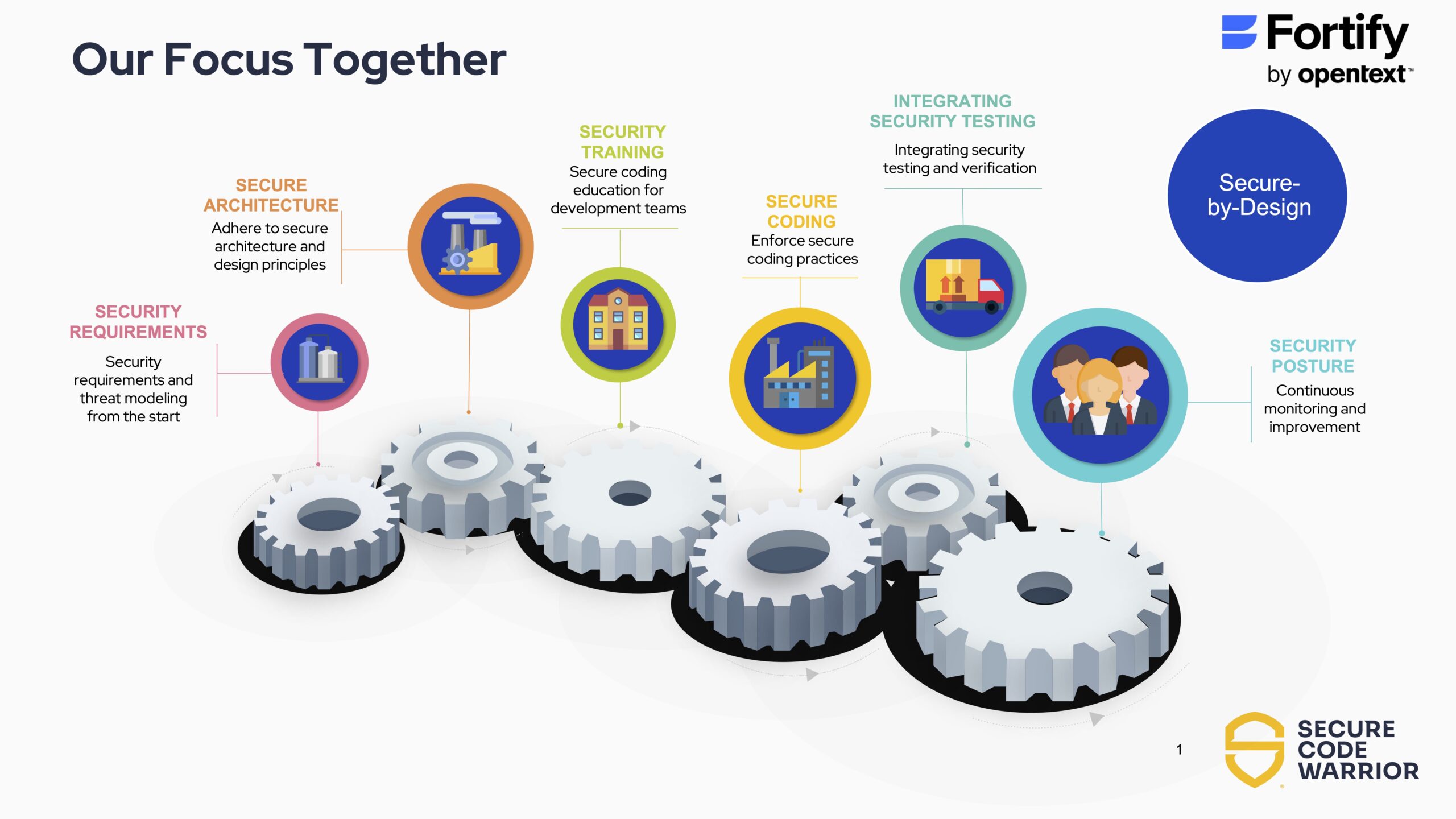
The overall goal is to reduce the level of friction application developers might encounter when they need to learn new security skills, he added.
Additionally, organizations from a billing perspective now have a single point of contact to streamline vendor management, noted Thomas.
Application developers, as a rule, don’t set out to create an insecure application, but unless issues are surfaced at the time they are writing code they will continue to make mistakes. In addition to surfacing issues using code scanning tools, OpenText is now making it easier for developers to resolve issues by consulting the corpus of application security training content that Secure Code Warrior curates.
Additionally, Secure Code Warrior will use findings from OpenText code analysis tools to extend the scope of the training it provides, and OpenText will be exposing that training content to the portfolio of artificial intelligence (AI) agents it is developing.
That’s crucial in an era where more security issues are being traced back to flaws that were created when an application was developed. A recent OpenText survey, for example, found that 62% of respondents who worked for organizations impacted by a ransomware attack in the past year later discovered the issue originated with a partner that was part of their software supply chain.
In general, the training provided by Secure Code Warrior is more effective because of the gamification techniques it employs to engage application developers more deeply to enable organizations to embrace secure-by-design principles, said Thomas.
Less clear, however, is the degree to which organizations are prioritizing the adoption of best DevSecOps practices. A Techstrong Research survey finds less than half (47%) of respondents work for organizations that regularly employ best DevSecOps practices. Only 54% of respondents regularly practice code scanning for vulnerabilities during development, while 40% conduct security testing, the survey finds.
On the plus side, a full 59% of respondents said they are also making further investments in application security, with 19% describing their investment level as high. Nearly two-thirds (64%) also noted they are specifically investing in a code scanning tool, with 24% describing those investments as high.
Ultimately, the easier it becomes for developers to do the right thing the more likely it becomes that application security will generally improve. There may never come a day when there is such a thing as perfect security but it should be feasible to eliminate the types of security mistakes that are all too commonly made today. After all, the simple truth of the matter is that when it comes to vulnerabilities in software there are simply too many of them for cybercriminals to easily exploit.



