Legit Security today extended its ability to scan for secrets in software to include any that might reside in the personal GitHub repositories of application developers.
The company is making that capability available both as a stand-alone product that individual developers can deploy and as a feature of its application security posture management (ASPM) platform.
Lior Barak, chief product officer for Legit Security, said this capability will prove crucial because it enables DevSecOps teams to address this issue long before secrets are inadvertently embedded in a corporate repository through which they might be distributed across a software supply chain.
As part of that effort, the company has also revamped the user interface of its ASPM platform to include a dashboard to provide a more comprehensive view of remediation efforts, that are ranked based on severity and potential risk to the business.
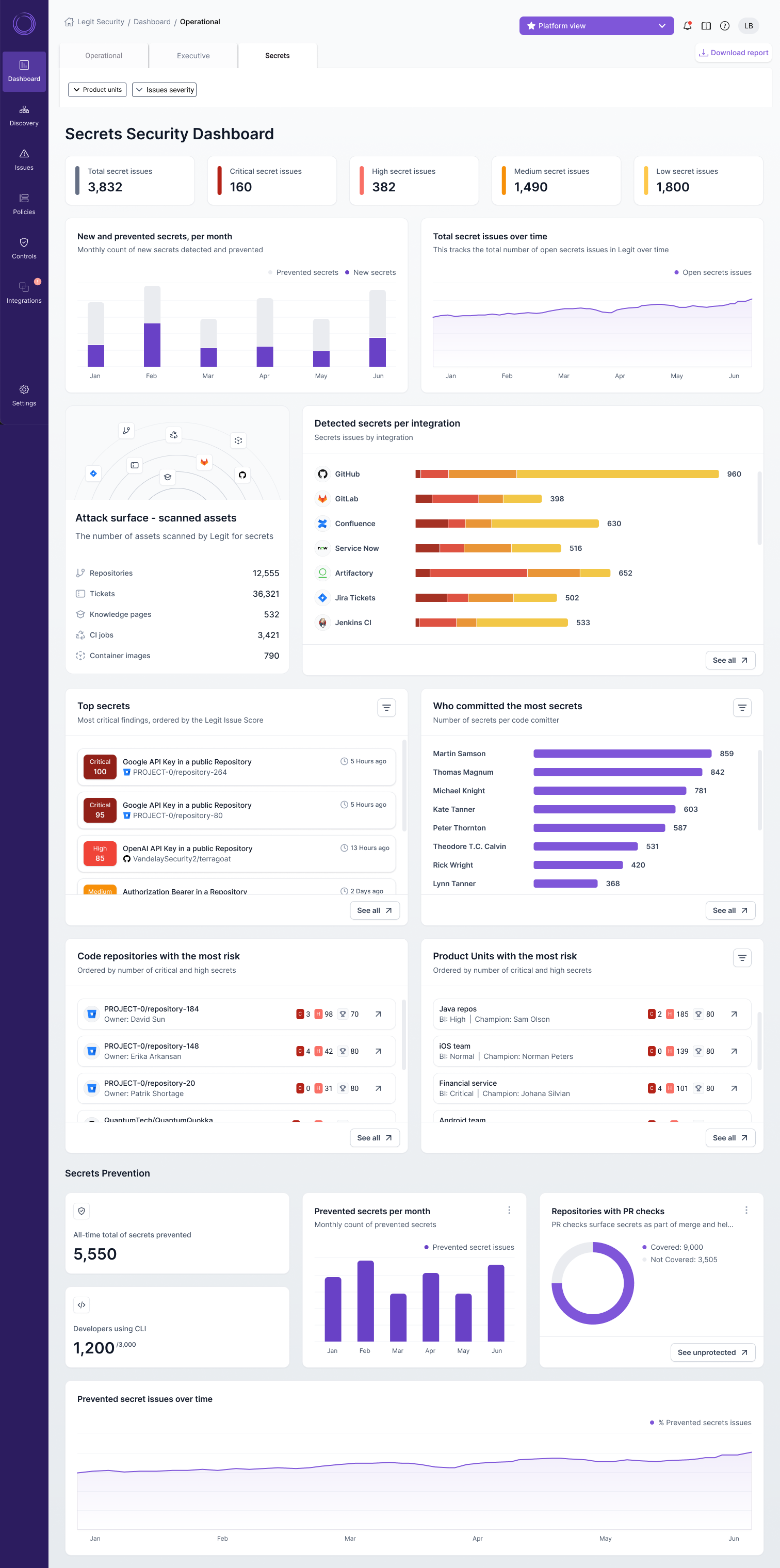
Legit Security makes use of artificial intelligence (AI) to more precisely identify secrets in applications that have been inadvertently exposed by developers. Those secrets are often stored in plain text that cybercriminals can easily discover using their own scanning tools. That issue has become more pressing, now that secrets in addition to enabling end users to access applications are also being assigned to software components and machines that cybercriminals have learned to target.
As software is developed secrets can now be found everywhere from messaging platforms such as Slack to ticketing systems and artifact registries, noted Barak.
It’s not clear how aggressively application development teams are scanning for those secrets. A Techstrong Research survey finds less than half (47%) of respondents work for organizations that regularly employ best DevSecOps practices. Only 54% of respondents regularly practice code scanning for vulnerabilities during development, while 40% conduct security testing, the survey finds.
On the plus side, a full 59% of respondents said they are also making further investments in application security, with 19% describing their investment level as high. Nearly two-thirds (64%) also noted they are specifically investing in a code scanning tool, with 24% describing those investments as high.
Of course, scanning for secrets is only one element of DevSecOps workflows but as regulations become increasingly stringent, tolerance for such mistakes is dropping. Organizations in the months ahead will soon find that regulatory bodies are going to levy heavier penalties for deploying insecure software.
At the same time, cybercriminals are similarly investing in AI tools to scan for any weakness in the software supply chain, especially application secrets that make it relatively trivial for them to gain initial access to applications. After that, escalating privileges in a way that enables them to deploy malware across a distributed computing environment becomes much simpler.
They say for want of a nail a war can be lost. In the case of application security, that proverbial nail is an application secret stored in plain text. The challenge now is making sure all those secrets are discovered before any bad actor can exploit them with predictable catastrophic consequences.



